Internet forensics mapping
As part of the research developed during his residency (Nov & Dec 2016) at Hangar, Vladan Joeler (Sharle Lab) in collaboration with Critical Interface Politics Research Group (Joana Moll y Andrea Noni) has designed a series of maps that show some of the complex structures of the Internet.
Main topics covered in this research project: #Internet Physicality; #Geopolitics of the Internet; #Algorithmic Governance; #Interface Politics; #Internet Backbone; #Data flows & Sustainability; #Cognitive Capitalism; #Social Engineering; #Surveillance; #Online Tracking; #Data Commodi fication; #Data Privacy.
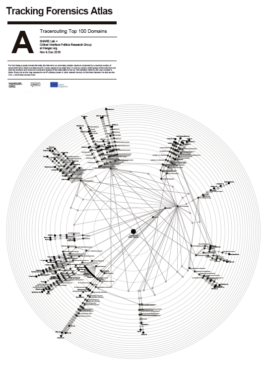
Map A: Tracerouting Top 100 Domains
Far from being a purely immaterial entity, the Internet is an extremely complex structure composed by a massive number of actors that have a direct and deep impact in every aspect of our daily lives. In order to create a wider picture of the data flow and map key locations and actors we conducted analysis of the data paths to the top 100 websites visited by the users located in Spain. Every dot on this map represents one IP address (router or other network device) and the lines between the dots are the links – cables that connect them.
Map B: Mapping ISP: Guifi.net
First step of understanding network infrastructure is to understand the structure of our nearest network, network runned and owned by our Internet service provider. During our research we had a luck to explore and map one of the World’s biggest bottom- up, citizen-driven, free, open and neutral telecommunications network- guifi-net. This unique network, based mostly in Catalonia consist of more than 32.500 operating nodes. This map is the network graph of guifi-net, where each dot represent one router, server of a computer and each line represent a link, a wireless or a cable that connect them.
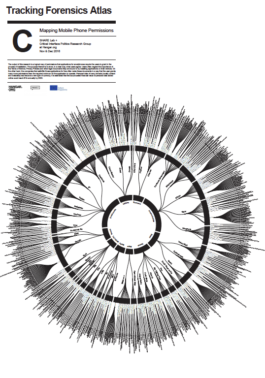
Map C: Mapping Mobile Phone Permissions
The output of this research is a logical map of permissions that applications for smartphones require the users to grant in the process of installation. The purpose thereof is to show, in a clear way, what users agree. Users often neglect the importance of the Terms of Service, Privacy Policies and other legal documents they are bound to by installing applications on their devices. On the other hand, the companies that sell/offer those applications for free often make these documents in a way that the user grants many more permissions than the required minimum for the application to operate. Personal data of many formats (mostly content and metadata) has become a new type of currency. It is estimated that the accumulated financial value of personal data stored
online could reach €1tn annually by 2020.
Categories: Publications | Tags: publicacions